This video really opened my eyes in how I view passwords and password security.
Most people on the internet don’t know what a random password is or how to keep it secure. They are also about a decade behind what enterprises are doing in regards to password complexity.
While enterprise password requirements are good in a way they haven’t changed in the last 10 or so years.

And the Password complexity requirements are not really enough as we shall see.
Password cracking techniques have evolved in the last 10 years. And these techniques are accessible to a greater number of people.
Password re-use: using the same password across multiple sites
Rule Generation – Previous data: if your password was FluffyUnicorn02 a few months ago then to crack now they would guess FluffyUnicorn03, FluffyUnicorn04 … etc
Rule Generation – Source based: LinkedInPassword for Linked in then would guess FacebookPassword for Facebook.
The Pattern based or Topologies is where it gets really interesting.
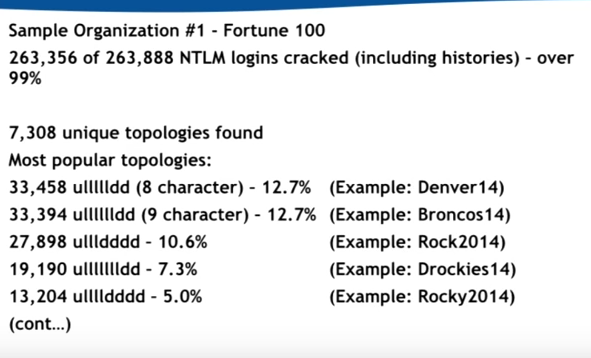
Cracking Passwords based on Topologies
Password crackers are not going to try and brute force the entire password range. They are going to try and narrow it down based on certain patterns, this is because when people create passwords it is hardly ever truly random.

In fact people tend to use similar topologies when creating passwords, brute forcing the most popular topologies makes much more sense for password crackers.
My personal password Strategy
Personally I use Lastpass for 99% of my password storage needs. Lastpass is an online password manager that stores, generates and autofills passwords for you. This way I only need to remember one password! For an extra layer of security I have added 2 factor authentication onto this account, so even if someone were to guess my password they wouldn’t be able to access my vault of passwords without my phone.
Since watching this video when I generate passwords with Lastpass I make them at least 20 characters long. And because this is somewhat randomly generated there is almost no chance of it matching any popular topology patterns.
Another way to generate passwords to avoid the top topologies is the dice method. This is essentially just a string of 6 random words based on what you get as the result of 30 dice rolls.
It would also take hackers many lifetimes to brute force the password so I feel safe now.

The above screenshot shows how long a 20 character length password generated with Lastpass would take to crack with an average laptop.
Now I feel pretty confident that my passwords are safe and my passwords can’t be guessed even with powerful computers.